我是废物
来
CRYPTO
where_is_n
没有模数,也就是已知c、e,求解明文
正常来说公式是m = pow(c, d, N)
在仅已知c、e的情况下,几乎不能反推出其他的参数,放弃
TakeFlagEasily
题目:
#!/usr/local/bin/python
from random import getrandbits
p = 2**607 - 1
a = getrandbits(607)
b = getrandbits(607)
print("a =", a)
print("b =", b)
try:
seed = int(input("Give me your seed: "))
res = int(input("Give me your result: "))
except:
print("Get out!")
exit(0)
r = getrandbits(22)
for _ in range(r):
seed = (a * seed + b) % p
if seed == res:
print("Take your flag:", open("flag.txt").read())
else:
print("Sorry, not this way.")LCG算法,但我哪会CRYPTO啊,只能是日常撞大运了
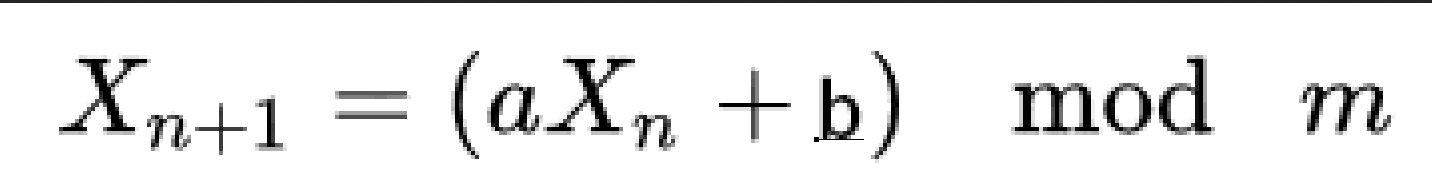
ctf之lcg算法_小健健健的博客-CSDN博客_lcg算法
不知道从哪抄来的解seed脚本(但是没用上):
#Xn=(a-1 (Xn+1 - b))%n
MMI = lambda A, n,s=1,t=0,N=0: (n < 2 and t%N or MMI(n, A%n, t, s-A//n*t, N or n),-1)[n<1]
ani=MMI(a,n)
for i in range(r):
seed = (ani*(seed-b))%n
print(seed)撞大运:
from hashlib import sha256
import random
from pwn import *
import string
for i in range(10000000):
context.log_level = 'debug'
p = remote("47.95.195.171", 8888)
p.recvuntil(b'a = ')
a = p.recvuntil(b'\n').strip().decode()
p.recvuntil(b'b = ')
b = p.recvuntil(b'\n').strip().decode()
pp = 2**607 - 1
seed = 1
p.recvuntil(b'Give me your seed: ')
p.sendline(str(seed))
a = int(a)
b = int(b)
for _ in range(3):
seed = (a * seed + b) % pp
p.recvuntil(b'Give me your result: ')
p.sendline(str(seed))
if p.recv(5) == b'Sorry':
p.close()
continue
else:
break
MISC
所见即所思
所思即所想有一大堆的不可打印字符,大概看一下是U+200E和U+200F,推测零宽字符隐写
Offdev.net - Zero-width space steganography javascript demo (mzy0.com)

Realworld
你真的懂校纪吗1.0
让我想起来S3C的那道题了
大同小异
题目:
#!/usr/bin/python3.8
# -*- coding: UTF-8 -*-
import random, string, subprocess, os, sys
from signal import alarm
import hashlib
class myrandom:
def __init__(self,seed,n,s):
self.x = seed
self.n = n
self.s = s
def next(self):
x = int((self.x ** 2) // (10 ** (self.s // 2))) % self.n
self.x = x
high = (int(hashlib.sha256(str(x).encode()).hexdigest(),16) >> 16) & (2 ** 16 - 1)
low = x & (2 ** 16 - 1)
result = high << 16 | low
return result % 7
def proof_of_work():
random.seed(os.urandom(8))
proof = ''.join([random.choice(string.ascii_letters+string.digits) for _ in range(20)])
digest = hashlib.sha256(proof.encode()).hexdigest()
print("sha256(XXXX+%s) == %s" % (proof[4:],digest))
print("Give me XXXX:")
x = input()
if len(x) != 4 or hashlib.sha256((x + proof[4:]).encode()).hexdigest() != digest:
print("你怎么考上东秦的")
exit()
def Check():
alarm(60)
proof_of_work()
alarm(100)
n = 10000000000
s = 4
seed = os.urandom(4)
seed = int.from_bytes(seed,byteorder = "big")
r = myrandom(seed,n,s)
score = 0
fanqiang = 0
for i in range(100):
try:
fanqiang = r.next()
print("翻墙次数:{}".format(fanqiang))
if fanqiang >= 0 and fanqiang <= 1:
status = input("处分类型:")
score += (status == "警告")
elif fanqiang >= 2 and fanqiang <= 3:
status = input("处分类型:")
score += (status == "严重警告")
elif fanqiang >= 4 and fanqiang <= 5:
status = input("处分类型:")
score += (status == "记过")
elif fanqiang >= 4 and fanqiang <= 5:
status = input("处分类型:")
score += (status == "留校察看")
else:
status = input("处分类型:")
score += (status == "开除学籍")
if score > 60:
print("你是懂东秦校纪的")
os.system("cat ./flag")
break
except:
exit(0)
def main():
print("+----------------------------+")
print("| 你懂东秦校纪吗 |")
print("| |")
print("| 1. 你这算是问对人了 |")
print("| 2. 别问,问就是退学 |")
print("+----------------------------+")
# cmd = raw_input(">> ")
cmd = input(">> ")
if cmd == '1':
Check()
else:
print("好退")
if __name__ == "__main__":
main()脚本:
from hashlib import sha256
import random
from pwn import *
import string
context.log_level = 'debug'
dir = string.ascii_letters + string.digits
p = remote("47.95.195.171", 6666)
p.sendlineafter(b'+----------------------------+', '1')
p.recvuntil(b'sha256(XXXX+')
salt = p.recv(16).strip().decode()
p.recvuntil(b') == ')
hash = p.recv(64).strip().decode()
while True:
rand_str = (''.join([random.choice(dir) for _ in range(4)])) + salt
if sha256(rand_str.encode()).hexdigest() == hash:
print("",rand_str[:4])
p.sendlineafter(b'Give me XXXX:', rand_str[:4])
break
for i in range(60):
p.recvuntil('翻墙次数:'.encode("utf-8"))
fanqiang = int(p.recv(1).strip().decode())
if fanqiang >= 0 and fanqiang <= 1:
p.sendline("警告".encode("utf-8"))
elif fanqiang >= 2 and fanqiang <= 3:
p.sendline("严重警告".encode("utf-8"))
elif fanqiang >= 4 and fanqiang <= 5:
p.sendline("记过".encode("utf-8"))
elif fanqiang >= 4 and fanqiang <= 5:
p.sendline("留校察看".encode("utf-8"))
else:
p.sendline("开除学籍".encode("utf-8"))
p.interactive()

flag{d6d80e8e1681b34328ee4c475b638ea0567a8e4a}
你真的懂校纪吗2.0
上面的check()改了一下,但是思路都一样
题目(部分):
def proof_of_work():
chal = ''.join(random.choice(string.letters+string.digits) for _ in xrange(16))
print('chal: '+chal)
sol = input('sol: ')
if len(sol) != 4 or not sha256(chal + sol).hexdigest().startswith('00000'):
print('你怎么考上东秦的')
exit()小改一下:
from hashlib import sha256
import random
from pwn import *
import string
context.log_level = 'debug'
dir = string.ascii_letters + string.digits
p = remote("47.95.195.171", 7777)
p.sendlineafter(b'+----------------------------+', '1')
p.recvuntil(b'chal: ')
chal = p.recv(16).strip().decode()
while True:
rand_str = (''.join([random.choice(dir) for _ in range(4)]))
if hashlib.sha256((chal + rand_str).encode('utf-8')).hexdigest().startswith('00000'):
print("",rand_str[:4])
p.sendlineafter(b'sol: ', rand_str[:4])
break
p.sendlineafter(b'Code: ', b'啥玩意啊')
p.interactive()之后那个Code长度要小于1024,还给了vm的二进制文件,估计是PWN,就此结束(
完整题目:
#!/usr/bin/python3.8
# -*- coding: UTF-8 -*-
import random, string, subprocess, os, sys
from signal import alarm
import hashlib
def proof_of_work():
chal = ''.join(random.choice(string.letters+string.digits) for _ in xrange(16))
print('chal: '+chal)
sol = input('sol: ')
if len(sol) != 4 or not sha256(chal + sol).hexdigest().startswith('00000'):
print('你怎么考上东秦的')
exit()
def Check():
alarm(60)
proof_of_work()
alarm(100)
code = input("Code: ")
try:
if len(code) > 0x400 :
print("Error.")
sys.exit(0)
except Exception as e:
print("Error.")
sys.exit(0)
score = 0
new_score = 0
fanqiang = 0
while True:
try:
fanqiang = random.randint(0,7)
io = process("./vm")
# context.log_level = 'debug'
io.sendlineafter('input your opcode:\n', code)
io.sendline(fanqiang)
if fanqiang >= 0 and fanqiang <= 1:
status = io.readline(timeout=8)[:-1]
new_score += (status == "警告")
elif fanqiang >= 2 and fanqiang <= 3:
status = io.readline(timeout=8)[:-1]
new_score += (status == "严重警告")
elif fanqiang >= 4 and fanqiang <= 5:
status = io.readline(timeout=8)[:-1]
new_score += (status == "记过")
elif fanqiang >= 4 and fanqiang <= 5:
status = io.readline(timeout=8)[:-1]
new_score += (status == "留校察看")
else:
status = io.readline(timeout=8)[:-1]
new_score += (status == "开除学籍")
io.close()
if new_score == score:
break
score = new_score
if score > 100:
print("你是懂东秦校纪的")
os.system("cat ./flag")
break
except Exception as e:
io.close()
break
def main():
print("+----------------------------+")
print("| 你懂东秦校纪吗 |")
print("| |")
print("| 1. 你这算是问对人了 |")
print("| 2. 别问,问就是退学 |")
print("+----------------------------+")
# cmd = raw_input(">> ")
cmd = input(">> ")
if cmd == '1':
Check()
else:
print("好退")
if __name__ == "__main__":
main()
WEB
EzSSRF(baby)
题目:
<?php
highlight_file(__file__);
function curl($url){
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_HEADER, 0);
echo curl_exec($ch);
curl_close($ch);
}
if(isset($_GET['url'])){
$url = $_GET['url'];
if(preg_match('/localhost|127.0.0.1|http\:\/\//is', $url,$match))
{
//你知道ssrf什么意思嘛,给你个`公网`的hint罢,快去hint.php康康
die('Too young,Too simple!');
}
curl($url);
}
if(isset($_GET['info'])){
phpinfo();
}
?>SSRF,用file://协议读文件即可,但是flag到底放在哪里了呢?

EzRCE
需要分别绕过前缀和后缀
前面的"/var/www/html/"用../进行目录穿越,测试可行
124.222.182.202:30002/?rce=../../../../../../../../../../../../../var/www/html/index
伪协议行不通,跨站也不行,作罢。

WEB复现
Ezssrf


由phpinfo得到网段
Hostname:Port 172.19.0.3:80
扫扫扫:

这次我可把flag放到根目录了,让我康康是谁访问不到了呀?
但是好心的我留了个上传后门呢1
通过字典扫描可以发现/upload目录,redis利用
使用gopherus生成payload

修改ip和port,编码后传入

(关于这里郑佬踩的坑:

URL编码时没有编码全部字符,CaptfEncoder可以更换为编码全部字符)
81.70.101.23:8848/b1ub1u.php?url=172.19.0.2/upload/mnhhh.php

Ezssrf(baby)

扫扫扫:

81.70.101.23:8838/b1ub1u.php?url=172.31.0.2/f1ag.php

Ezrce
Easy?

蚁剑连上124.222.182.202:30002/?rce=./../../tmp/mnh











Comments | NOTHING